These properties have effect only when mode=dynamic-keys.
authentication-types (multiple choice of wpa-psk, wpa2-psk, wpa-eap and wpa2-eap; default value is empty) : Set of supported authentication types. Access point will advertise supported authentication types, and client will connect to access point only if supports any of the advertised authentication types.
unicast-ciphers (multiple choice of tkip, aes-ccm; default value is empty) : Access point advertises that it supports specified ciphers. Client attempts connection only to access points that supports at least one of the specified ciphers. One of the ciphers will be used to encrypt unicast frames that are sent between access point and station.
group-ciphers (multiple choice of tkip, aes-ccm; default value is empty) : Access point advertises one of these ciphers, and uses it to encrypt all broadcast and multicast frames. Client attempts connection only to access points that use one of the specified group ciphers.
tkip - Temporal Key Integrity Protocol - encryption protocol, compatible with lagacy WEP equipment, but enhanced to correct some of WEP flaws
aes-ccm - more secure WPA encryption protocol, based on the reliable AES (Advanced Encryption Standard). Networks free of WEP legacy should use only this
group-key-update (time interval in the 30s..1h range; default value: 5m) : Controls how often access point updates group key. This key is used to encrypt all broadcast and multicast frames. This property has no effect in station mode.
wpa-pre-shared-key, wpa2-pre-shared-key (text) : WPA and WPA2 pre-shared key mode requires all devices in a BSS to have common secret key. Value of this key can be an arbitrary text.
RouterOS also allows to override pre-shared key value for specific clients, using either private-pre-shared-key property in the access-list, or the Mikrotik-Wireless-Psk attribute in the RADIUS MAC authentication response. This is an extension. These properties have effect only when authentication-types contains either wpa-psk or wpa2-psk.
wpa-pre-shared-key is used for wpa-psk authentication type. wpa2-pre-shared-key is used for wpa2-psk.
WPA EAP properties
These properties have effect only when authentication-types contains wpa-eap or wpa2-eap, and mode=dynamic-keys.
eap-methods (array of eap-tls, passthrough) :
eap-tls - Use built-in EAP TLS authentication. Both client and server certificates are supported. See description of tls-mode and tls-certificate properties.
passthrough - Access point will relay authentication process to the RADIUS server. This value is ignored in station mode. Order of values is significant for access point configuration, it is used by access point when offering specified methods to clients. Example: Access point uses security-profile where eap-methods=eap-tls,passthrough: Access point offers EAP-TLS method to the client. Client refuses. Access point starts relaying EAP communication to the radius server.
supplicant-identity (text; default value is same as system/identity of router at the moment of profile creation) : EAP identity that is sent by client at the beginning of EAP authentication. This value is used as a value for User-Name attribute in RADIUS messages sent by RADIUS EAP accounting and RADIUS EAP pass-through authentication.
tls-mode (one of verify-certificate, dont-verify-certificate, no-certificates; default value: no-certificates) :
verify-certificate - Require remote device to have valid certificate. Check that it is signed by known certificate authority. No additional identity verification is done.
Note: Certificate may include information about time period during which it is valid. If router has incorrect time and date, it may reject valid certificate because router's clock is outside that period.
See also: certificate configuration.
dont-verify-certificate - Do not check certificate of the remote device. Access point will not require client to provide certificate.
no-certificates - Do not use certificates. TLS session is established using 2048 bit anonymous Diffie-Hellman key exchange. When using first two modes, remote device has to support one of the "RC4-MD5", "RC4-SHA" or "DES-CBC3-SHA" TLS cipher suites. In the last mode remote device must support "ADH-DES-CBC3-SHA" cipher suite. This property has effect only when eap-methods contains eap-tls.
tls-certificate (none or name of certificate; default value: none) : Access point always needs certificate when configured with tls-mode=verify-certificate, or tls-mode=dont-verify-certificate. Client needs certificate only if access point is configured with tls-mode=verify-certificate. In this case client needs valid certificate that is signed by CA known to the access point. This property has effect only if tls-mode≠no-certificates. This property has effect only when eap-methods contains eap-tls.
RADIUS properties
radius-mac-authentication (yes or no; default value: no) : This property affects the way how access point processes clients that are not found in the access-list.
no - allow or reject client authentication based on the value of default-authentication property of the wireless interface.
yes - Query RADIUS server using MAC address of client as user name. With this setting the value of default-authentication has no effect.
radius-mac-accounting (yes or no; default value: no) : (needs editing)
radius-eap-accounting (yes or no; default value: no) : (needs editing)
interim-update (time interval; default value: 0) : When RADIUS accounting is used, access point periodically sends accounting information updates to the RADIUS server. This property specifies default update interval that can be overridden by the RADIUS server using Acct-Interim-Interval attribute.
radius-mac-format (one of XX:XX:XX:XX:XX:XX, XXXX:XXXX:XXXX, XXXXXX:XXXXXX, XX-XX-XX-XX-XX-XX, XXXXXX-XXXXXX, XXXXXXXXXXXX, XX XX XX XX XX XX; default value: XX:XX:XX:XX:XX:XX) : Controls how MAC address of the client is encoded by access point in the User-Name attribute of the MAC authentication and MAC accounting RADIUS requests.
radius-mac-mode (one of as-username, as-username-and-password; default value: as-username) : By default access point uses empty password, when sending Access-Request during MAC authentication. When this property is set to as-username-and-password, access point will use the same value for User-Password attribute as for the User-Name attribute.
radius-mac-caching (either disabled or time interval; default value: disabled) : If this value is set to time interval, the access point will cache RADIUS MAC authentication responses for specified time, and will not contact RADIUS server if matching cache entry already exists. Value disabled will disable cache, access point will always contact RADIUS server.
WEP properties
These properties have effect only when mode is static-keys-required or static-keys-optional. See section "Wireless#Statically_configured_WEP_keys".
static-key-0, static-key-1, static-key-2, static-key-3 (hexadecimal representation of the key. Length of key must be appropriate for selected algorithm - see section "Statically configured WEP keys; default value is empty) : (needs editing)
static-algo-0, static-algo-1, static-algo-2, static-algo-3 (one of none, 40bit-wep, 104bit-wep, tkip or aes-ccm; default value: none) : Encryption algorithm to use with the corresponding key.
static-transmit-key (one of key-0, key-1, key-2 or key-3; default value: key-0) : Access point will use the specified key to encrypt frames for clients that do not use private key. Access point will also use this key to encrypt broadcast and multicast frames. Client will use the specified key to encrypt frames if static-sta-private-algo=none. If corresponding static-algo- property has value none, frame will be sent unencrypted (when mode=static-keys-optional) or will not be sent at all (when mode=static-keys-required).
static-sta-private-key (hexadecimal representation of the key. Length of key must be appropriate for selected algorithm - see section "Statically configured WEP keys") : This property is used only in station mode. Access point uses corresponding key either from private-key property of access-list, or from Mikrotik-Wireless-Enc-Key attribute in RADIUS Access-Accept MAC authentication response.
static-sta-private-algo (one of none, 40bit-wep, 104bit-wep, tkip or aes-ccm) : Encryption algorithm to use with station private key. Value none disables use of the private key. This property is used only in station mode. Access point has to get corresponding value either from private-algo property of access-list, or from Mikrotik-Wireless-Enc-Algo attribute in RADIUS Access-Accept MAC authentication response. Station private key replaces key 0 for unicast frames. Station will not use private key to decrypt broadcast frames.
Management frame protection
Used for: Deauthentication attack prevention, MAC address cloning issue.
RouterOS implements proprietary management frame protection algorithm based on shared secret. Management frame protection means that RouterOS wireless device is able to verify source of management frame and confirm that particular frame is not malicious. This feature allows to withstand deauthentication and disassociation attacks on RouterOS based wireless devices.
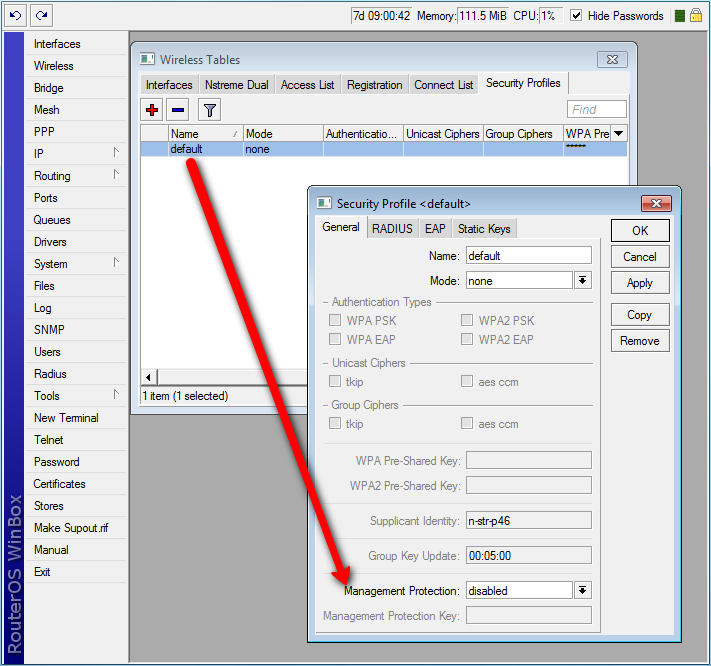
Management protection mode is configured in security-profile with management-protection setting. Possible values are: disabled - management protection is disabled (default), allowed - use management protection if supported by remote party (for AP - allow both, non-management protection and management protection clients, for client - connect both to APs with and without management protection), required - establish association only with remote devices that support management protection (for AP - accept only clients that support management protection, for client - connect only to APs that support management protection).
Management protection shared secret is configured with security-profile management-protection-key setting.
When interface is in AP mode, default management protection key (configured in security-profile) can be overridded by key specified in access-list or RADIUS attribute.
[admin@mikrotik] /interface wireless security-profiles> print 0 name="default" mode=none authentication-types="" unicast-ciphers="" group-ciphers="" wpa-pre-shared-key="" wpa2-pre-shared-key="" supplicant-identity="n-str-p46" eap-methods=passthrough tls-mode=no-certificates tls-certificate=none static-algo-0=none static-key-0="" static-algo-1=none static-key-1="" static-algo-2=none static-key-2="" static-algo-3=none static-key-3="" static-transmit-key=key-0 static-sta-private-algo=none static-sta-private-key="" radius-mac-authentication=no radius-mac-accounting=no radius-eap-accounting=no interim-update=0s radius-mac-format=XX:XX:XX:XX:XX:XX radius-mac-mode=as-username radius-mac-caching=disabled group-key-update=5m management-protection=disabled management-protection-key=""
[admin@mikrotik] /interface wireless security-profiles> set default management-protection= allowed disabled required
Operation details
RADIUS MAC authentication
Note: RAIDUS MAC authentication is used by access point for clients that are not found in the access-list, similarly to the default-authentication property of the wireless interface. It controls whether client is allowed to proceed with authentication, or is rejected immediately.
When radius-mac-authentication=yes, access point queries RADIUS server by sending Access-Request with the following attributes:
User-Name - Client MAC address. This is encoded as specified by the radius-mac-format setting. Default encoding is "XX:XX:XX:XX:XX:XX".
Nas-Port-Id - name of wireless interface.
User-Password - When radius-mac-mode=as-username-and-password this is set to the same value as User-Name. Otherwise this attribute is empty.
Calling-Station-Id - Client MAC address, encoded as "XX-XX-XX-XX-XX-XX".
Called-Station-Id - MAC address and SSID of the access point, encoded as "XX-XX-XX-XX-XX-XX:SSID" (minus separated pairs of MAC address digits, followed by colon, followed by SSID value).
Acct-Session-Id - Added when radius-mac-accounting=yes.
When access point receives Access-Accept or Access-Reject response from the RADIUS server, it stores the response and either allows or rejects client. Access point uses following RADIUS attributes from the Access-Accept response:
Ascend-Data-Rate
Ascend-Xmit-Rate
Mikrotik-Wireless-Forward - Same as access-list forwarding.
Mikrotik-Wireless-Enc-Algo - Same as access-list private-algo.
Mikrotik-Wireless-Enc-Key - Same as access-list private-key.
Mikrotik-Wireless-Psk - Same as access-list private-pre-shared-key.
Session-Timeout - Time, after which client will be disconnected.
Acct-Interim-Interval - Overrides value of interim-update.
Class - If present, value of this attribute is saved and included in Accounting-Request messages.
Caching
Caching of RADIUS MAC authentication was added to support RADIUS authentication for clients that require from the access point very quick response to the association request. Such clients time out before response from RADIUS server is received. Access point caches authentication response for some time and can immediately reply to the repeated association request from the same client.
RADIUS EAP pass-through authentication
When using WPA EAP authentication type, clients that have passed MAC authentication are required to perform EAP authentication before being authorized to pass data on wireless network. With pass-through EAP method the access point will relay authentication to RADIUS server, and use following attributes in the Access-Request RADIUS message:
User-Name - EAP supplicant identity. This value is configured in the supplicant-identity property of the client security profile.
Nas-Port-Id - name of wireless interface.
Calling-Station-Id - Client MAC address, encoded as "XX-XX-XX-XX-XX-XX".
Called-Station-Id - MAC address and SSID of the access point, encoded as "XX-XX-XX-XX-XX-XX:SSID" (pairs of MAC address digits separated by minus sign, followed by colon, followed by SSID value).
Acct-Session-Id - Added when radius-eap-accounting=yes.
Acct-Multi-Session-Id - MAC address of access point and client, and unique 8 byte value, that is shared for all accounting sessions that share single EAP authentication. Encoded as AA-AA-AA-AA-AA-AA-CC-CC-CC-CC-CC-CC-XX-XX-XX-XX-XX-XX-XX-XX. Added when radius-eap-accounting=yes.
Access point uses following RADIUS attributes from the Access-Accept server response:
Class - If present, value of this attribute is saved and included in Accounting-Request messages.
Session-Timeout - Time, after which client will be disconnected. Additionally, access point will remember authentication result, and if during this time client reconnects, it will be authorized immediately, without repeating EAP authentication.
Acct-Interim-Interval - Overrides value of interim-update.
Statically configured WEP keys
Different algorithms require different length of keys:
40bit-wep - 10 hexadecimal digits (40 bits). If key is longer, only first 40 bits are used.
104bit-wep - 26 hexadecimal digits (104 bits). If key is longer, only first 104 bits are used.
tkip - At least 64 hexadecimal digits (256 bits).
aes-ccm - At least 32 hexadecimal digits (128 bits).
Key must contain even number of hexadecimal digits.
WDS security configuration
WDS links can use all available security features. However, they require careful configuration of security parameters.
It is possible to use one security profile for all clients, and different security profiles for WDS links. Security profile for WDS link is specified in connect-list. Access point always checks connect list before establishing WDS link with another access point, and used security settings from matching connect list entry. WDS link will work when each access point will have connect list entry that matches the other device, has connect=yes and specifies compatible security-profile.
WDS and WPA/WPA2
If access point uses security profile with mode=dynamic-keys, then encryption will be used for all WDS links. Since WPA authentication and key exchange is not symmetrical, one of the access points will act as a client for the purpose of establishing secure connection. This is similar to how static-mesh and dynamic-mesh WDS modes work. Some problems, like single sided WDS link between two incorrectly configured access points that use non-mesh mode, is not possible if WPA encryption is enabled. However, non-mesh modes with WPA still have other issues (like constant reconnection attempts in case of configuration mismatch) that are solved by use of the -mesh WDS modes.
In general, WPA properties on both access points that establish WPA protected WDS link have to match. These properties are authentication-types, unicast-ciphers, group-ciphers. For non-mesh WDS mode these properties need to have the same values on both devices. In mesh WDS mode each access point has to support the other one as a client.
Theoretically it is possible to use RADIUS MAC authentication and other RADIUS services with WDS links. However, only one access point will interact with the RADIUS server, the other access point will behave as a client.
Implementation of eap-tls EAP method in RouterOS is particularly well suited for WDS link encryption. tls-mode=no-certificates requires no additional configuration, and provides very strong encryption.
WDS and WEP
mode, static-sta-private-key and static-sta-private-algo parameters in the security profile assigned to the WDS link need to have the same values on both access points that establish WDS link with WPA encryption.
Security profile and access point matching in the connect list
Client uses value of connect-list security-profile property to match only those access points that support necessary security.
mode=static-keys-required and mode=static-keys-optional matches only access points with the same mode in interface security-profile.
If mode=dynamic-keys, then connect list entry matches if all of the authentication-types, unicast-ciphers and group-ciphers contain at least one value that is advertised by access point.
authentication-types (multiple choice of wpa-psk, wpa2-psk, wpa-eap and wpa2-eap; default value is empty) : Set of supported authentication types. Access point will advertise supported authentication types, and client will connect to access point only if supports any of the advertised authentication types.
unicast-ciphers (multiple choice of tkip, aes-ccm; default value is empty) : Access point advertises that it supports specified ciphers. Client attempts connection only to access points that supports at least one of the specified ciphers. One of the ciphers will be used to encrypt unicast frames that are sent between access point and station.
group-ciphers (multiple choice of tkip, aes-ccm; default value is empty) : Access point advertises one of these ciphers, and uses it to encrypt all broadcast and multicast frames. Client attempts connection only to access points that use one of the specified group ciphers.
tkip - Temporal Key Integrity Protocol - encryption protocol, compatible with lagacy WEP equipment, but enhanced to correct some of WEP flaws
aes-ccm - more secure WPA encryption protocol, based on the reliable AES (Advanced Encryption Standard). Networks free of WEP legacy should use only this
group-key-update (time interval in the 30s..1h range; default value: 5m) : Controls how often access point updates group key. This key is used to encrypt all broadcast and multicast frames. This property has no effect in station mode.
wpa-pre-shared-key, wpa2-pre-shared-key (text) : WPA and WPA2 pre-shared key mode requires all devices in a BSS to have common secret key. Value of this key can be an arbitrary text.
RouterOS also allows to override pre-shared key value for specific clients, using either private-pre-shared-key property in the access-list, or the Mikrotik-Wireless-Psk attribute in the RADIUS MAC authentication response. This is an extension. These properties have effect only when authentication-types contains either wpa-psk or wpa2-psk.
wpa-pre-shared-key is used for wpa-psk authentication type. wpa2-pre-shared-key is used for wpa2-psk.
WPA EAP properties
These properties have effect only when authentication-types contains wpa-eap or wpa2-eap, and mode=dynamic-keys.
eap-methods (array of eap-tls, passthrough) :
eap-tls - Use built-in EAP TLS authentication. Both client and server certificates are supported. See description of tls-mode and tls-certificate properties.
passthrough - Access point will relay authentication process to the RADIUS server. This value is ignored in station mode. Order of values is significant for access point configuration, it is used by access point when offering specified methods to clients. Example: Access point uses security-profile where eap-methods=eap-tls,passthrough: Access point offers EAP-TLS method to the client. Client refuses. Access point starts relaying EAP communication to the radius server.
supplicant-identity (text; default value is same as system/identity of router at the moment of profile creation) : EAP identity that is sent by client at the beginning of EAP authentication. This value is used as a value for User-Name attribute in RADIUS messages sent by RADIUS EAP accounting and RADIUS EAP pass-through authentication.
tls-mode (one of verify-certificate, dont-verify-certificate, no-certificates; default value: no-certificates) :
verify-certificate - Require remote device to have valid certificate. Check that it is signed by known certificate authority. No additional identity verification is done.
Note: Certificate may include information about time period during which it is valid. If router has incorrect time and date, it may reject valid certificate because router's clock is outside that period.
See also: certificate configuration.
dont-verify-certificate - Do not check certificate of the remote device. Access point will not require client to provide certificate.
no-certificates - Do not use certificates. TLS session is established using 2048 bit anonymous Diffie-Hellman key exchange. When using first two modes, remote device has to support one of the "RC4-MD5", "RC4-SHA" or "DES-CBC3-SHA" TLS cipher suites. In the last mode remote device must support "ADH-DES-CBC3-SHA" cipher suite. This property has effect only when eap-methods contains eap-tls.
tls-certificate (none or name of certificate; default value: none) : Access point always needs certificate when configured with tls-mode=verify-certificate, or tls-mode=dont-verify-certificate. Client needs certificate only if access point is configured with tls-mode=verify-certificate. In this case client needs valid certificate that is signed by CA known to the access point. This property has effect only if tls-mode≠no-certificates. This property has effect only when eap-methods contains eap-tls.
RADIUS properties
radius-mac-authentication (yes or no; default value: no) : This property affects the way how access point processes clients that are not found in the access-list.
no - allow or reject client authentication based on the value of default-authentication property of the wireless interface.
yes - Query RADIUS server using MAC address of client as user name. With this setting the value of default-authentication has no effect.
radius-mac-accounting (yes or no; default value: no) : (needs editing)
radius-eap-accounting (yes or no; default value: no) : (needs editing)
interim-update (time interval; default value: 0) : When RADIUS accounting is used, access point periodically sends accounting information updates to the RADIUS server. This property specifies default update interval that can be overridden by the RADIUS server using Acct-Interim-Interval attribute.
radius-mac-format (one of XX:XX:XX:XX:XX:XX, XXXX:XXXX:XXXX, XXXXXX:XXXXXX, XX-XX-XX-XX-XX-XX, XXXXXX-XXXXXX, XXXXXXXXXXXX, XX XX XX XX XX XX; default value: XX:XX:XX:XX:XX:XX) : Controls how MAC address of the client is encoded by access point in the User-Name attribute of the MAC authentication and MAC accounting RADIUS requests.
radius-mac-mode (one of as-username, as-username-and-password; default value: as-username) : By default access point uses empty password, when sending Access-Request during MAC authentication. When this property is set to as-username-and-password, access point will use the same value for User-Password attribute as for the User-Name attribute.
radius-mac-caching (either disabled or time interval; default value: disabled) : If this value is set to time interval, the access point will cache RADIUS MAC authentication responses for specified time, and will not contact RADIUS server if matching cache entry already exists. Value disabled will disable cache, access point will always contact RADIUS server.
WEP properties
These properties have effect only when mode is static-keys-required or static-keys-optional. See section "Wireless#Statically_configured_WEP_keys".
static-key-0, static-key-1, static-key-2, static-key-3 (hexadecimal representation of the key. Length of key must be appropriate for selected algorithm - see section "Statically configured WEP keys; default value is empty) : (needs editing)
static-algo-0, static-algo-1, static-algo-2, static-algo-3 (one of none, 40bit-wep, 104bit-wep, tkip or aes-ccm; default value: none) : Encryption algorithm to use with the corresponding key.
static-transmit-key (one of key-0, key-1, key-2 or key-3; default value: key-0) : Access point will use the specified key to encrypt frames for clients that do not use private key. Access point will also use this key to encrypt broadcast and multicast frames. Client will use the specified key to encrypt frames if static-sta-private-algo=none. If corresponding static-algo- property has value none, frame will be sent unencrypted (when mode=static-keys-optional) or will not be sent at all (when mode=static-keys-required).
static-sta-private-key (hexadecimal representation of the key. Length of key must be appropriate for selected algorithm - see section "Statically configured WEP keys") : This property is used only in station mode. Access point uses corresponding key either from private-key property of access-list, or from Mikrotik-Wireless-Enc-Key attribute in RADIUS Access-Accept MAC authentication response.
static-sta-private-algo (one of none, 40bit-wep, 104bit-wep, tkip or aes-ccm) : Encryption algorithm to use with station private key. Value none disables use of the private key. This property is used only in station mode. Access point has to get corresponding value either from private-algo property of access-list, or from Mikrotik-Wireless-Enc-Algo attribute in RADIUS Access-Accept MAC authentication response. Station private key replaces key 0 for unicast frames. Station will not use private key to decrypt broadcast frames.
Management frame protection
Used for: Deauthentication attack prevention, MAC address cloning issue.
RouterOS implements proprietary management frame protection algorithm based on shared secret. Management frame protection means that RouterOS wireless device is able to verify source of management frame and confirm that particular frame is not malicious. This feature allows to withstand deauthentication and disassociation attacks on RouterOS based wireless devices.
Management protection mode is configured in security-profile with management-protection setting. Possible values are: disabled - management protection is disabled (default), allowed - use management protection if supported by remote party (for AP - allow both, non-management protection and management protection clients, for client - connect both to APs with and without management protection), required - establish association only with remote devices that support management protection (for AP - accept only clients that support management protection, for client - connect only to APs that support management protection).
Management protection shared secret is configured with security-profile management-protection-key setting.
When interface is in AP mode, default management protection key (configured in security-profile) can be overridded by key specified in access-list or RADIUS attribute.
[admin@mikrotik] /interface wireless security-profiles> print 0 name="default" mode=none authentication-types="" unicast-ciphers="" group-ciphers="" wpa-pre-shared-key="" wpa2-pre-shared-key="" supplicant-identity="n-str-p46" eap-methods=passthrough tls-mode=no-certificates tls-certificate=none static-algo-0=none static-key-0="" static-algo-1=none static-key-1="" static-algo-2=none static-key-2="" static-algo-3=none static-key-3="" static-transmit-key=key-0 static-sta-private-algo=none static-sta-private-key="" radius-mac-authentication=no radius-mac-accounting=no radius-eap-accounting=no interim-update=0s radius-mac-format=XX:XX:XX:XX:XX:XX radius-mac-mode=as-username radius-mac-caching=disabled group-key-update=5m management-protection=disabled management-protection-key=""
[admin@mikrotik] /interface wireless security-profiles> set default management-protection= allowed disabled required

Operation details
RADIUS MAC authentication
Note: RAIDUS MAC authentication is used by access point for clients that are not found in the access-list, similarly to the default-authentication property of the wireless interface. It controls whether client is allowed to proceed with authentication, or is rejected immediately.
When radius-mac-authentication=yes, access point queries RADIUS server by sending Access-Request with the following attributes:
User-Name - Client MAC address. This is encoded as specified by the radius-mac-format setting. Default encoding is "XX:XX:XX:XX:XX:XX".
Nas-Port-Id - name of wireless interface.
User-Password - When radius-mac-mode=as-username-and-password this is set to the same value as User-Name. Otherwise this attribute is empty.
Calling-Station-Id - Client MAC address, encoded as "XX-XX-XX-XX-XX-XX".
Called-Station-Id - MAC address and SSID of the access point, encoded as "XX-XX-XX-XX-XX-XX:SSID" (minus separated pairs of MAC address digits, followed by colon, followed by SSID value).
Acct-Session-Id - Added when radius-mac-accounting=yes.
When access point receives Access-Accept or Access-Reject response from the RADIUS server, it stores the response and either allows or rejects client. Access point uses following RADIUS attributes from the Access-Accept response:
Ascend-Data-Rate
Ascend-Xmit-Rate
Mikrotik-Wireless-Forward - Same as access-list forwarding.
Mikrotik-Wireless-Enc-Algo - Same as access-list private-algo.
Mikrotik-Wireless-Enc-Key - Same as access-list private-key.
Mikrotik-Wireless-Psk - Same as access-list private-pre-shared-key.
Session-Timeout - Time, after which client will be disconnected.
Acct-Interim-Interval - Overrides value of interim-update.
Class - If present, value of this attribute is saved and included in Accounting-Request messages.
Caching
Caching of RADIUS MAC authentication was added to support RADIUS authentication for clients that require from the access point very quick response to the association request. Such clients time out before response from RADIUS server is received. Access point caches authentication response for some time and can immediately reply to the repeated association request from the same client.
RADIUS EAP pass-through authentication
When using WPA EAP authentication type, clients that have passed MAC authentication are required to perform EAP authentication before being authorized to pass data on wireless network. With pass-through EAP method the access point will relay authentication to RADIUS server, and use following attributes in the Access-Request RADIUS message:
User-Name - EAP supplicant identity. This value is configured in the supplicant-identity property of the client security profile.
Nas-Port-Id - name of wireless interface.
Calling-Station-Id - Client MAC address, encoded as "XX-XX-XX-XX-XX-XX".
Called-Station-Id - MAC address and SSID of the access point, encoded as "XX-XX-XX-XX-XX-XX:SSID" (pairs of MAC address digits separated by minus sign, followed by colon, followed by SSID value).
Acct-Session-Id - Added when radius-eap-accounting=yes.
Acct-Multi-Session-Id - MAC address of access point and client, and unique 8 byte value, that is shared for all accounting sessions that share single EAP authentication. Encoded as AA-AA-AA-AA-AA-AA-CC-CC-CC-CC-CC-CC-XX-XX-XX-XX-XX-XX-XX-XX. Added when radius-eap-accounting=yes.
Access point uses following RADIUS attributes from the Access-Accept server response:
Class - If present, value of this attribute is saved and included in Accounting-Request messages.
Session-Timeout - Time, after which client will be disconnected. Additionally, access point will remember authentication result, and if during this time client reconnects, it will be authorized immediately, without repeating EAP authentication.
Acct-Interim-Interval - Overrides value of interim-update.
Statically configured WEP keys
Different algorithms require different length of keys:
40bit-wep - 10 hexadecimal digits (40 bits). If key is longer, only first 40 bits are used.
104bit-wep - 26 hexadecimal digits (104 bits). If key is longer, only first 104 bits are used.
tkip - At least 64 hexadecimal digits (256 bits).
aes-ccm - At least 32 hexadecimal digits (128 bits).
Key must contain even number of hexadecimal digits.
WDS security configuration
WDS links can use all available security features. However, they require careful configuration of security parameters.
It is possible to use one security profile for all clients, and different security profiles for WDS links. Security profile for WDS link is specified in connect-list. Access point always checks connect list before establishing WDS link with another access point, and used security settings from matching connect list entry. WDS link will work when each access point will have connect list entry that matches the other device, has connect=yes and specifies compatible security-profile.
WDS and WPA/WPA2
If access point uses security profile with mode=dynamic-keys, then encryption will be used for all WDS links. Since WPA authentication and key exchange is not symmetrical, one of the access points will act as a client for the purpose of establishing secure connection. This is similar to how static-mesh and dynamic-mesh WDS modes work. Some problems, like single sided WDS link between two incorrectly configured access points that use non-mesh mode, is not possible if WPA encryption is enabled. However, non-mesh modes with WPA still have other issues (like constant reconnection attempts in case of configuration mismatch) that are solved by use of the -mesh WDS modes.
In general, WPA properties on both access points that establish WPA protected WDS link have to match. These properties are authentication-types, unicast-ciphers, group-ciphers. For non-mesh WDS mode these properties need to have the same values on both devices. In mesh WDS mode each access point has to support the other one as a client.
Theoretically it is possible to use RADIUS MAC authentication and other RADIUS services with WDS links. However, only one access point will interact with the RADIUS server, the other access point will behave as a client.
Implementation of eap-tls EAP method in RouterOS is particularly well suited for WDS link encryption. tls-mode=no-certificates requires no additional configuration, and provides very strong encryption.
WDS and WEP
mode, static-sta-private-key and static-sta-private-algo parameters in the security profile assigned to the WDS link need to have the same values on both access points that establish WDS link with WPA encryption.
Security profile and access point matching in the connect list
Client uses value of connect-list security-profile property to match only those access points that support necessary security.
mode=static-keys-required and mode=static-keys-optional matches only access points with the same mode in interface security-profile.
If mode=dynamic-keys, then connect list entry matches if all of the authentication-types, unicast-ciphers and group-ciphers contain at least one value that is advertised by access point.
0 Response to "WPA properties "
Post a Comment